Cybersecurity basics for beginners: A guide
Protect yourself online by familiarizing yourself with these cybersecurity basics, like types of cyberattacks and cybersecurity best practices to follow.

We use the internet for virtually every daily activity, but with more accounts, apps, and streaming services come more cybersecurity threats. In this guide, we’ll cover important cybersecurity basics, best practices to ward off cyberattacks, and how you can help protect your personal information while surfing the web with software like Norton 360 Deluxe.
What is cybersecurity?
Cybersecurity refers to every aspect of protecting critical systems, devices, and sensitive data against cyberattacks. From individual users to large multimillion-dollar corporations, having effective cybersecurity practices in place is essential for safeguarding your sensitive personal and financial information online.
Cybersecurity terms to know
Here are a few common cybersecurity terms you’ll come across — or may have already:
- Network: interconnected digital devices that can exchange information and resources with one another
- Internet protocol (IP) address: a unique numerical identifier assigned to every device or network with internet access
- Virtual private network (VPN): an encrypted internet connection from a device to a network
- Hacker (black hat): a malicious person who attempts to gain unauthorized access to a network with the intent to cause damage or theft
- Hacker (white hat): A person who attempts to gain unauthorized access to a network in order to identify and patch vulnerabilities in a security system
- Firewall: a network security feature designed to monitor incoming and outgoing network traffic in order to block unauthorized access
- Domain Name System (DNS): a directory of domain names that align with IP addresses so users can search via URLs
- Encryption: the process of scrambling readable text so that it can only be read by the person who has the encryption key
- Authentication: the process of verifying a user’s identity in order for them to access a system and/or data, like two-factor authentication
- Data breach: often the result of a successful cyberattack that results in the exposure of personal data, like credit card or Social Security numbers
We’ll cover more need-to-know terms as you continue to read through these cybersecurity basics.
Cybersecurity fundamentals
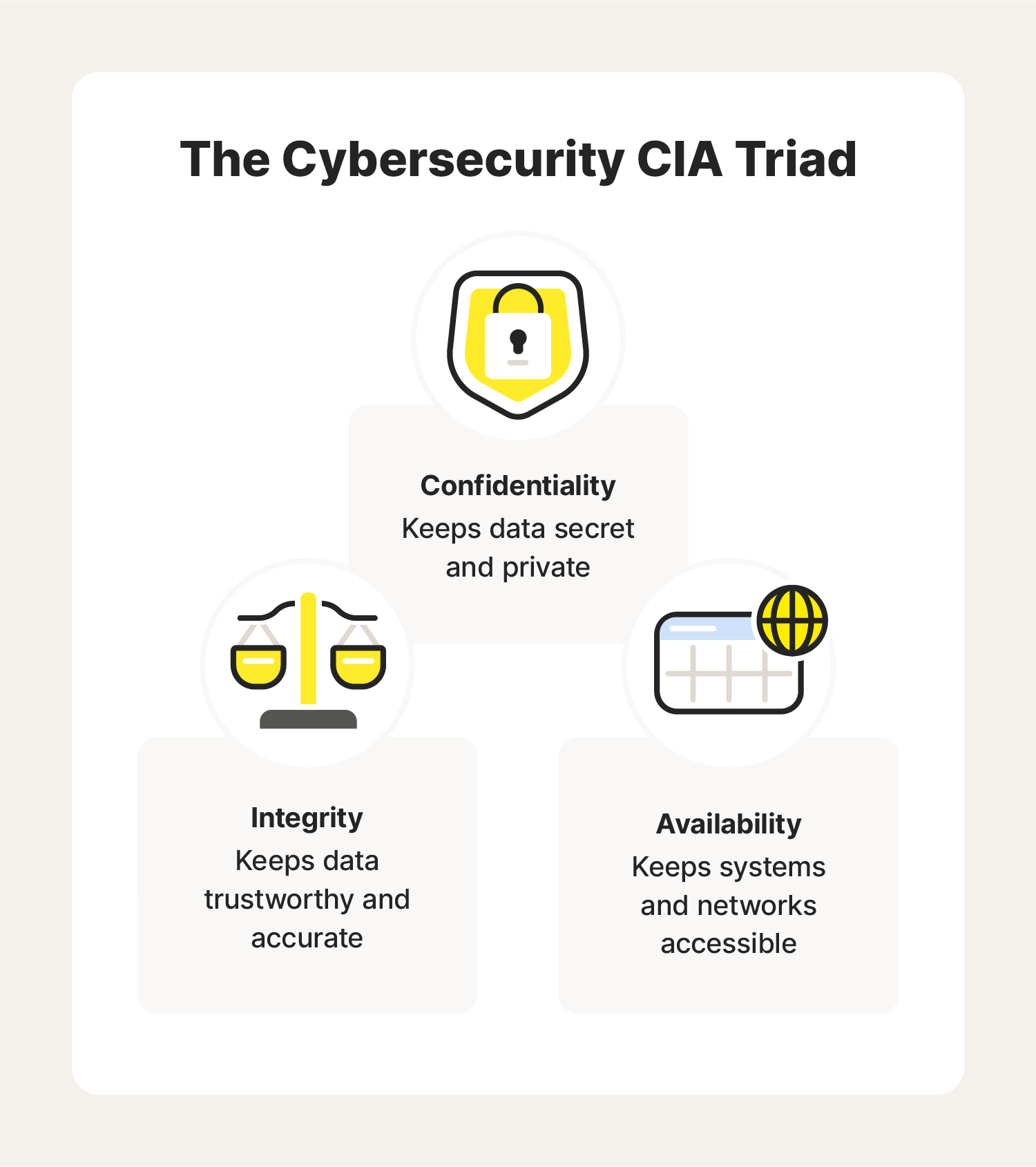
To grasp the fundamentals of cybersecurity, we’ll need to break down the CIA triad. The CIA triad refers to the three principles of cybersecurity: confidentiality, integrity, and availability.
The CIA triad model serves as the basis for the development of most cybersecurity systems. Ideally, you’ll want to meet all three standards to help protect yourself against cyberattacks.
Confidentiality
Confidentiality refers to the measures you take to ensure your data is kept secret or private. This includes personal information like:
- Credit card information
- Social Security numbers
- Physical addresses
- Medical records
- Account login information
Cybercriminals may make a direct attempt to steal this information with techniques like man-in-the-middle (MITM) attacks or phishing. Once the hackers have access to this data, they can take control of your accounts or sell the information on the black market.
However, human error and insufficient security protocols may also play a role in a confidentiality breach. For example, using weak passwords or leaving your computer unattended could put your sensitive data at risk.
Integrity
Integrity in cybersecurity means ensuring your data remains trustworthy, accurate, and safeguarded against unauthorized modification or destruction.
This can be done by:
- Using end-to-end encryption to protect sensitive data while in transit and at rest
- Setting access controls so only authorized personnel can access specific information
- Ensuring no one user is given enough access to be able to misuse a system on their own
- Backing up data
Maintaining integrity is especially important for sites or users that provide important information to the public or organizations that handle sensitive information. For example, when a hacker published a fake news story under the guise of the Associated Press in 2013, the Dow Jones Index slumped by 150 points when the public believed the White House and President Obama had been attacked.
Integrity attacks can have huge implications for individuals as well. For instance, if a cybercriminal is able to access a bank database, they could manipulate the automated routing process to steal money and account information.
Availability
Even with effective confidentiality and integrity practices in place, a cybersecurity system is useless if it’s not available to the user(s) it’s intended to serve. Availability ensures that systems, networks, and applications are functioning so authorized users can access data when they need to.
Here’s an example of availability most of us can relate to. When mandatory lockdowns during the COVID-19 pandemic prevented employees from returning to office, many were unable to access the business-critical data and applications they needed to do their jobs. Without a disaster recovery system in place—essentially, a backup plan—availability can be severely impacted in situations like:
- Natural disasters
- Power outages
- Deliberate cyberattacks, like denial-of-service (DoS) attacks or ransomware
6 types of cybersecurity attacks
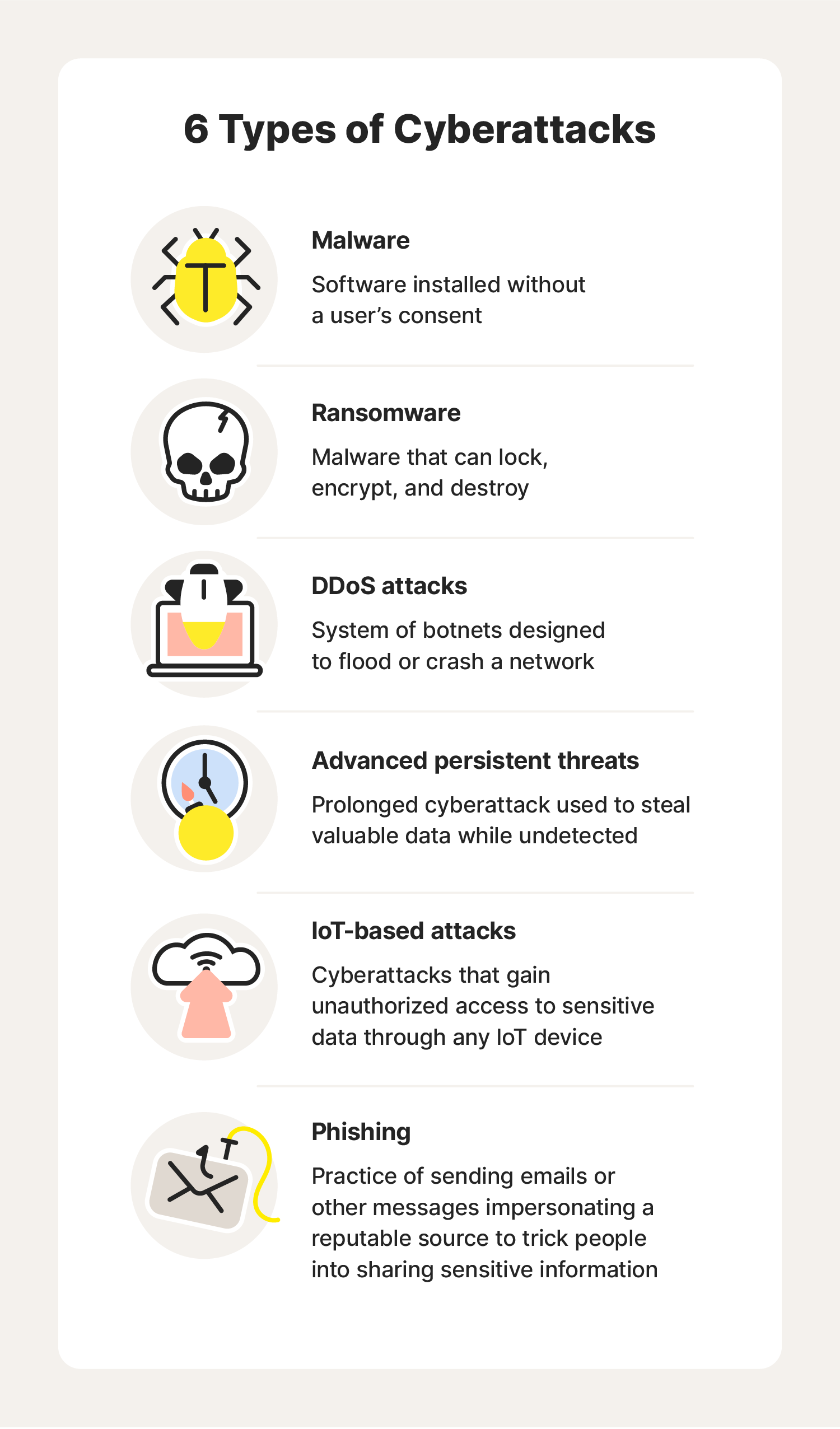
Cyberattacks are attempts by cybercriminals to access a computer network or system, typically with the goal of stealing or altering information or extorting money from the target.
Here are some of the most common ones to avoid.
1. Malware
Malware—short for “malicious software”—is software specifically designed to gain unauthorized access to or damage a device, typically without the owner’s knowledge (but not always). Common types of malware include:
- Trojan horses: malware disguised as a legitimate program that provides a hacker backdoor access to your computer
- Viruses: malware designed to change, corrupt, or destroy information that is then passed on to other systems, usually by otherwise benign means (like sending an email)
- Spyware: malware that is used by hackers to spy on your computer or mobile phone activities
- Worms: malware that can multiply and spread to other computers in the network
Most malware is unknowingly downloaded through this process:
- A hacker strategically places an infected link, file, or attachment in the path of a victim, usually through a phishing email or other social engineering tactic.
- The victim clicks on the malicious asset, triggering the malware to install onto their device.
- The hacker can use the malware to steal, compromise, and/or destroy data stored on the device.
Some cybercriminals will use USB sticks or flash drives to install malware onto a computer because it’s harder for some cybersecurity systems to detect. To avoid this, never leave your computer or other device logged in and unattended, and never insert an unfamiliar storage device into your computer.
2. Ransomware
Ransomware is malware that can lock, encrypt, and destroy personal files once it gains access to your computer. Like the name suggests, hackers typically use ransomware to extort money from their victims with promises of restoring the encrypted data.
Ransomware is a growing concern for organizations and individuals. More than 2,000 devices were infected with ransomware in 2021 alone, and hackers reaped more than $6 million in average payouts from victims in the U.S.
3. Distributed denial-of-service (DDoS) attacks
Similar to ransomware, distributed denial-of-service (DDoS) attacks also compromise computer availability. DDoS attacks are used by cybercriminals attempting to flood or crash a website by triggering traffic from millions of botnets. Here’s how it works:
- The hacker forms a “zombie network” of remotely controlled hacked computers called botnets.
- The hacker uses the zombie network to flood a targeted website or internet server with traffic, rendering it inoperable.
- Once the website or server crashes, both website administrators and online visitors won’t be able to access it.
At a minimum, a DDoS attack will result in a temporary loss of service or website performance issues that could impact revenue for a business. However, DDoS attacks can also be used to hold a site hostage until a ransom is paid. Some hackers have even used DDoS attacks as a smoke screen for other malicious activities.
4. Phishing
Have you ever received a message from one of your Facebook friends asking you to check out a deal they received on an expensive purse or new pair of sneakers? Chances are their account was hacked and used in a phishing scam.
Phishing is a cybercrime scammers use to try to lure sensitive information or data from you by impersonating a trustworthy source, like a friend or your bank. Phishers can trick you by sending links asking for personal information like your credit card or Social Security number through:
- Text message
- Phone calls
- Social media direct messages
Some phishing schemes are obvious—common red flags include poor grammar and odd-looking URLs. However, scammers are developing more sophisticated tactics to lure you into sharing your information.
For example, in 2018 phishers targeted Netflix users through an email stating the popular streaming platform was “having some trouble” accessing the customer’s billing information. The message asked users to click on a link to update their payment method. That link, of course, didn’t take users to Netflix but instead to a fake website created by the hackers.
5. Advanced persistent threats
Advanced persistent threats (APTs) are a type of attack on integrity used to infiltrate a network undetected for an extended period of time, all the while stealing valuable data without actually harming the network. APTs have the ability to destroy and manipulate files stored on computers and devices, targeting data like:
- Legal contracts
- Patent information
- Medical records
- Blueprints
- Financial documents
While large organizations and government platforms are typically the targets of APTs, individual users can also fall prey to this type of cyberattack. Some of the consequences of an APT attack include:
- Theft of intellectual property
- Distribution of sensitive information
- Site takeovers
- Session hijacking
- Destruction of data
6. IoT-based attacks
From STEM toys to smart home technology, the popularity of Internet of Things (IoT) devices is on the rise. It’s important to keep in mind that any device connected to the internet is prone to cyberattacks and should have cybersecurity measures in place to protect you and your personal information.
Cybercriminals take advantage of the security shortcomings characteristic of many IoT devices (IoT devices are particularly vulnerable to malware attacks and ransomware) to gain access to other devices on the network. Luckily, there are cybersecurity best practices to prevent these types of attacks.
10 cybersecurity best practices
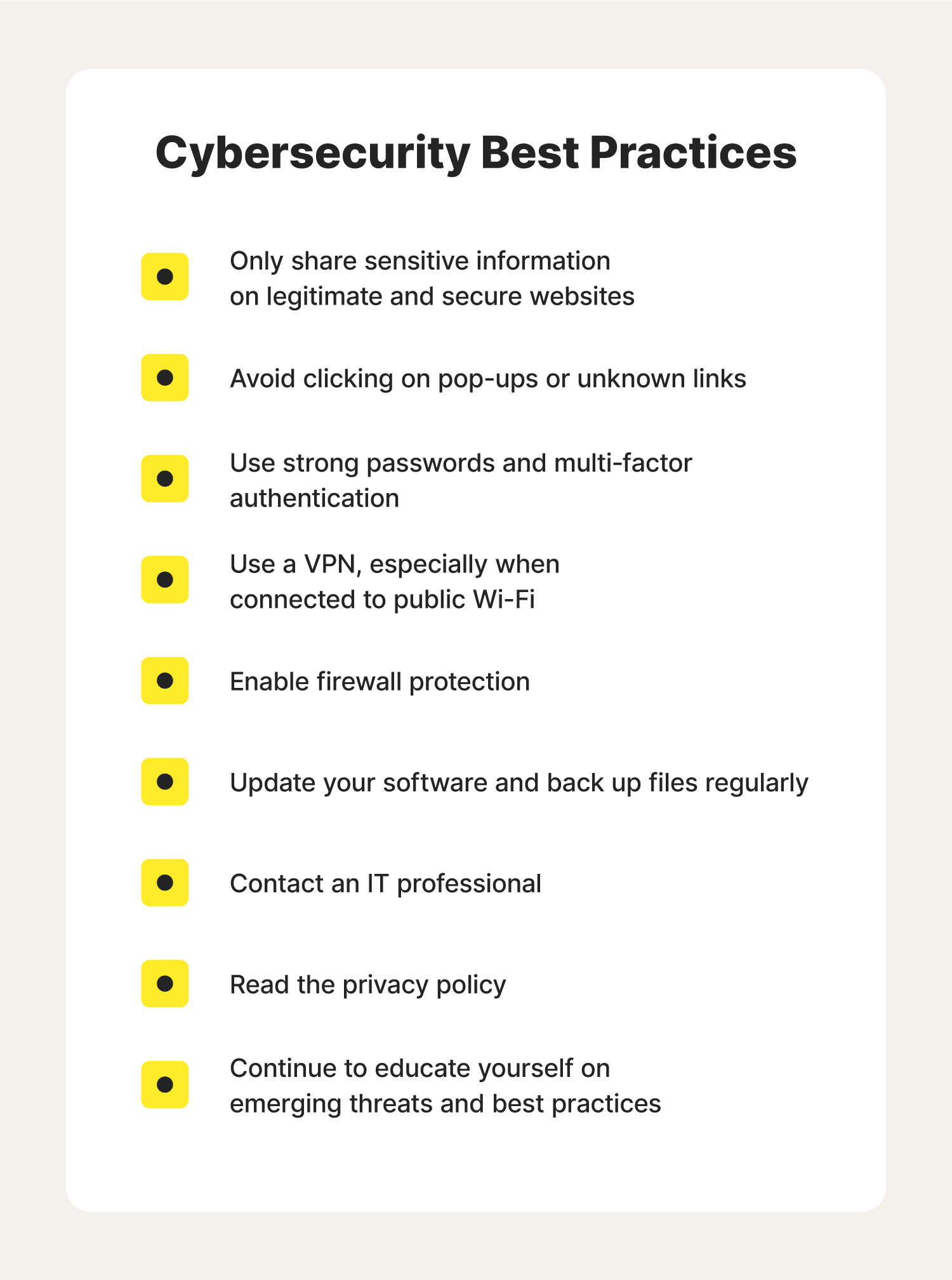
Cybersecurity best practices encompass some general best practices—like being cautious when engaging in online activities, safeguarding private information, and reaching out for help when you encounter something suspicious. Here’s a deeper dive into the 10 cybersecurity best practices every internet user should know and follow.
1. Safeguard your data
In your daily life, you probably avoid sharing personally identifiable information like your Social Security number or credit card number when answering an unsolicited phone call or text message. It’s important to exercise the same caution online. Cybercriminals have been known to impersonate trusted websites or authorities to trick you into providing personal information by:
- Creating email addresses and websites that look legitimate
- Faking caller ID information
- Taking over company social media accounts and sending seemingly legitimate messages
It might sound obvious, but do your due diligence before sharing this information. Hackers can use this information to hack personal accounts (like bank accounts), sell on the deep web, or even commit identity theft.
However, you may need to be more careful than you think. For instance, if you share a picture online that shows a whiteboard or computer screen in the background, you could accidentally reveal information someone shouldn’t see. Avoid oversharing on social media, and always check that a site requesting personal information is legitimate and secure.
2. Avoid pop-ups, unknown emails, and links
Beware of phishing. Phishers try to trick you into clicking on a link that may result in a security breach.
Phishers prey on internet users in hopes they will open pop-up windows or other malicious links that could have viruses and malware embedded in them. That’s why it’s important to be cautious of links and attachments in emails from senders you don’t recognize. With just one click, you could enable hackers to infiltrate your entire computer network.
Here’s a rule to follow: Never enter personal information in response to an email, pop-up webpage, or any other form of communication you didn’t initiate. Phishing can lead to identity theft. It’s also the way most ransomware attacks occur.
3. Use strong password protection and authentication
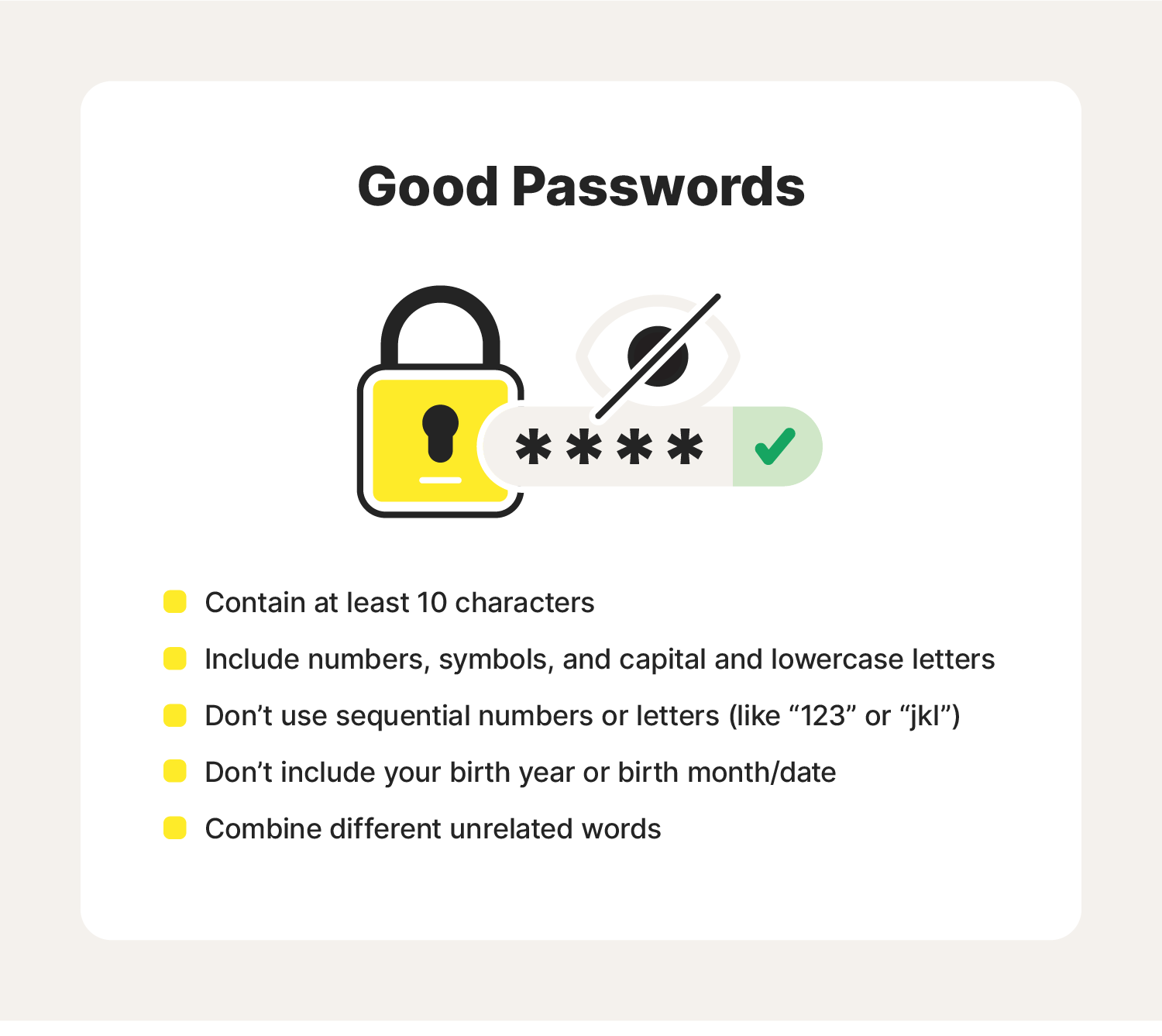
Strong, complex passwords can help stop cyberthieves from accessing your information. Simple passwords—think “12345” or your spouse's/child’s name—can make access easy. If a cybercriminal figures out your password, it could give them access to your network or account information. Creating unique, complex passwords is essential.
It’s also a smart idea to change your passwords on a regular basis. Changing and remembering all of your passwords may be challenging, but a password manager can help.
Another way to protect your account access is by enabling multi-factor authentication. This adds an additional layer of protection by asking you to take at least one extra step—such as providing a temporary code that is sent to your smartphone—to log in.
4. Connect to secure Wi-Fi
Home Wi-Fi networks should be secure, encrypted, and hidden. You can add an additional layer of protection by using a virtual private network (VPN). A VPN is a service that provides online privacy and anonymity by creating a private network from a public internet connection.
Free public Wi-Fi networks in places like coffee shops can put your data at risk of being intercepted. A VPN encrypts your connection so your online activity, including the links you click or the files you download, can’t be accessed by cybercriminals or other snoops.
But keep in mind that some VPNs are safer than others. Norton VPN provides powerful VPN protection that can help keep your information private, even when using public Wi-Fi.
5. Enable firewall protection
Having a firewall for your home network is the first line of defense in helping protect data against cyberattacks. Firewalls prevent unauthorized users from accessing your websites, mail services, and other sources of information that can be accessed from the web.
Think of a firewall as a gatekeeper to your computer. You want to keep your sensitive data in and keep prying eyes and malware out. A firewall monitors network traffic and enforces rules about access set in conjunction with other layers of security.
6. Invest in security systems
Everyday internet users might hesitate when considering the cost of investing in a quality security system. That usually includes protections like:
- Strong antivirus and malware detection
- External hard drives that back up data
- A VPN to keep internet browsing private
- Parental controls
- Site screening to block fake sites that steal passwords
- A password manager to create, store, and protect strong passwords
- Regular system checks
Even though a quality security system can be expensive, all of the devices you use at work and at home should have the added protection of cybersecurity software. Get Norton 360 Deluxe to help protect your devices against the wide range of today’s cyber threats.
7. Update your security software and back up your files
Following IT security best practices means keeping your security software, web browsers, and operating systems updated with the latest protections. Antivirus and anti-malware protections are frequently revised to target and respond to new cyber threats.
You should also secure and back up files regularly in case of a data breach or a malware attack. Your most important files should be stored offline on an external hard drive or in the cloud.
8. Contact an IT professional
IT professionals are your friends in regard to all things cybersecurity. Reach out to your security provider or other trusted tech professional about information security.
It’s a good idea to talk to IT if:
- You’re troubleshooting a software or hardware issue
- You’ve received a security warning from your internet security software
- You plan on traveling and using public Wi-Fi
Remember to make sure IT is, well, IT. Beware of tech support scams. You might receive a phishing email from someone claiming to be from IT. Their goal is to trick you into installing malware on your computer or mobile device or providing sensitive data. Don’t provide any information. Instead, contact your security service provider right away.
9. Read the Privacy Policy
It’s not enough to practice good cybersecurity habits yourself—if you’re shopping online or sharing private information with an individual or company, you should also ensure they’re implementing the appropriate cybersecurity measures to keep your data safe.
If you’re unfamiliar with a website or vendor, take a look at their website privacy policy to ensure their data privacy and protection process are compliant. This policy should list:
- The purpose of collecting personal data
- How and why that information may be shared
- Your rights regarding the processing of your personal data
If their privacy policy fails to provide this information—or if the site isn’t able to provide you with a policy—your information likely isn’t being sufficiently protected.
10. Embrace education and training
While cybersecurity software can protect against some cyberattacks, the biggest threat to your network is you—74% of data breaches are caused by human error and negligence, like misconfiguring databases or falling for a phishing scam. Take the time to educate yourself on the latest cybersecurity threats and best practices. Here are a few suggestions to help you stay on top of the evolving cybersecurity landscape:
- Subscribe to a tech newsletter
- Read up on local privacy and data protection regulations
- Follow your security provider on social media
A little technical savvy helps, too. Learning basic computer hardware terms, software skills, and security components can save time when you contact support, and they need quick access and information to resolve an issue.
Only you can help prevent cyberattacks
Knowing these cybersecurity basics can help strengthen your breach vulnerabilities. Remember: Just one click on a corrupt link could let a hacker in.
A strong cybersecurity system like Norton 360 Deluxe can help protect your personal information while you’re browsing online. Staying on top of cybersecurity best practices and using reliable online security software could mean the difference between a secure network and an unsecured one.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.